I've set up two 7.6 Nodes and joined them into a cluster. These use a Postgres database so no SQL required. I browse to the Control Center to configure SSL Certificates. Apparently my notes say replacing the SSL certificate on the first node fixed the second node, let's see if that's still the case!
We browse to Certificates.
I'll now import my CA Root certificate here
You can browse to the CER file next
Once imported your appliance will trust certificates issued by your CA.
The generate option in the next Tab only changes the details on the self signed certificate. It doesn't generate a CSR, very wierd!! I can import a PEM certificate but I'll need to generate it with OpenSSL.
Here is the openssl.cfg file I used:
[ req ]
default_bits = 2048
default_keyfile = rui.key
distinguished_name = req_distinguished_name
encrypt_key = no
prompt = no
string_mask = nombstr
req_extensions = v3_req
[ v3_req ]
basicConstraints = CA:false
keyUsage = digitalSignature, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth, clientAuth
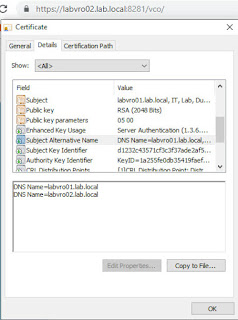
subjectAltName = DNS:labvro01.lab.local, DNS:labvro02.lab.local
[ req_distinguished_name ]
countryName = IE
stateOrProvinceName = IRL
localityName = Dublin
0.organizationName = Lab
organizationalUnitName = IT
commonName = labvro01.lab.local
I then created a PEM file from three files in the following order:
labvro01.lab.local.pem
Contents of Key File - labvro01.lab.local.key
Contents of new signed certificate file - labvro01.lab.local.cer
Contents of Root Cert from CA - Lab_Root_CA.cer
The cert appears on the second node automatically. I'll test the FQDN now using the different interfaces.
The certificate gives an error in Firefox but looks fine in Chrome.
Note: the Control Center URL on port 8283 is not signed by this certificate so you will still get warnings etc. This post deals with the VCO client.