This post will detail how to replace the self signed certificate on the 3 node Log Insight version 4.8 Cluster in my Lab.
Here is my cluster. I join some of them with an IP but it shouldn't matter:
Here is the SSL option under Configuration in the Administration section detailing the PEM requirements. Replacing the cert here has it copied to all nodes (as far as I recall) so it's a one step process, once you get the PEM certificate correct!
So, I've installed OpenSSL on my Domain Controller where my CA is. I need to generate a certificate request in order to sign it. I use OpenSSL to do this, then sign with the Windows CA, then I can export a PEM from that.
The OpenSSL binaries can be installed from here:
https://slproweb.com/products/Win32OpenSSL.html
The file C:\OpenSSL-Win64\bin\openssl.cfg should be backed up and then replaced with the following contents adjusted for your environment:
[ req ]
default_md
= sha512
default_bits
= 2048
default_keyfile
= rui.key
distinguished_name
= req_distinguished_name
encrypt_key
= no
prompt = no
string_mask
= nombstr
req_extensions
= v3_req
[ v3_req ]
basicConstraints
= CA:false
keyUsage =
digitalSignature, keyEncipherment, dataEncipherment
extendedKeyUsage
= serverAuth, clientAuth
subjectAltName = DNS:lablogi1.lab.local, DNS: lablogi2.lab.local, DNS: lablogi3.lab.local, DNS: lablogi4.lab.local, DNS:192.168.10.30, DNS:192.168.10.31, DNS:192.168.10.32, DNS:192.168.10.33, IP:192.168.10.30, IP:192.168.10.31, IP:192.168.10.32, IP:192.168.10.33
[
req_distinguished_name ]
countryName
= IE
stateOrProvinceName
= IRL
localityName
= Dublin
0.organizationName
= Lab
organizationalUnitName
= IT
commonName
= lablogi1.lab.local
You need to replace the values to reflect the FQDN and IPs you are using plus the correct owner details. Yes you need the IP to be listed twice, once as a DNS entry and again as an IP entry!
Now I can execute the command below in the C:\OpenSSL-Win64\bin directory and generate a CSR / Certificate Request File.
openssl
req -new -nodes -out C:\OpenSSL-Win64\bin\lablogi1.lab.local.csr -newkey
rsa:2048 -keyout C:\OpenSSL-Win64\bin\lablogi1.lab.local.key -config
C:\OpenSSL-Win64\bin\openssl.cfg
I've now got two new files, a .key file and the CSR. We'll open the CSR file and use it to generate a certificate from the CA. Browse to the CA web server http://localhost/certsrv if you're on the CA itself.
Click Request a Certificate
Click Advanced Certificate Request....
Click Submit a Certificate.....
Paste the CSR contents and choose the Web Server template
Click Base64 encoded and the Download certificate
We download this and name it lablogi1.cer and you should have the following file at this stage:
Last step - to create a PEM file I used the following command:
type lablogi1.lab.local.key lablogi1.cer lab_root_ca.cer > lablogi1.pem
(sequence is: key file, then loginsight signed certificate file, THEN the CA root cert)
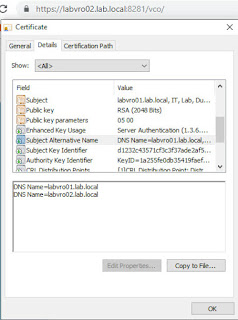
Now I can upload the PEM to Log Insight. You can get hold of the CA Root cer from the download certificate chain link earlier and then open the certificate, drill into the folder to see the Root Cert and perform an All Tasks, Export, Base-64 encoded X.509 (.CER) option.
Note: I was following other blog posts including VMware's. I couldn't believe how many I'd to go through to get the one that worked. They each had a different way of loading the PEM file. The one I'm listing worked for me but if my approach fails and you get an error uploading the certificate to Log Insight, head to google and try another like I did. It may be down to the version of Log Insight or some other reason but it was very frustrating!!
Now we've a signed certificate on our node. I should be able to browse to the VIP FQDN:
That's it! You can now browse to any of the four FQDN's to verify you are seeing a trusted and signed certificate.